Four FireEye researchers have found a way to steal fingerprints from
Android phones packing biometric sensors such as the Samsung Galaxy S5
and the HTC One Max.
The team found a forehead-slapping flaw in HTC One Max in which fingerprints are stored as an image file (dbgraw.bmp) in a open "world readable" folder.
"Any unprivileged processes or apps can steal user’s fingerprints by reading this file," the team says, adding that the images can be made into clear prints by adding some padding.
It is one of four vulnerability scenarios in which biometric data normally secure in an Android phone's TrustedZone can be pilfered.
One such scenario shows how attackers can have money transfers authenticated by throwing a fake lock screen prompting a victim to scan their fingerprints to unlock a device.
Yulong Zhang, Zhaofeng Chen, Hui Xue, Tao Wei say in the paper Fingerprints On Mobile Devices: Abusing and Leaking [PDF] presented at Black Hat in Las Vegas last week that most device manufacturers fail to use Android's Trust Zone protection to safeguard biometric data.
They say they are likely the first to reveal the threat.
"To make the situation even worse, each time the fingerprint sensor is used for auth operation, the auth framework will refresh that fingerprint bitmap to reflect the latest wiped finger," the team says.
"So the attacker can sit in the background and collect the fingerprint image of every swipe of the victim."
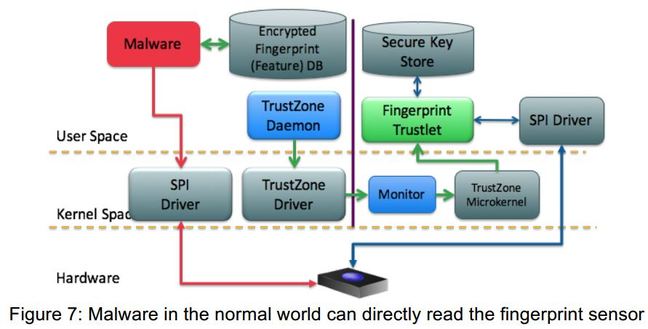 Even worse: kernel access permissions often only
restrict to root privilege, not system, meaning modified or 'rooted'
Android devices are at risk even if those protections are applied.
Even worse: kernel access permissions often only
restrict to root privilege, not system, meaning modified or 'rooted'
Android devices are at risk even if those protections are applied.
The team say attackers with some remote code execution exploits in hand can harvest these fingerprints en masse.
Attackers could in a probably less likely scenario add their fingerprints to a device which they have physical access to by uploading a print image. A disconnect between the number of authorised prints and actual authorised prints means the uploaded biometric could be seen as a "backdoor", the team says.
The researchers point out that this is a very serious mistake by citing research predicting that fingerprint scanners will exist in about half of all phones sold in 2019.
The risk could be considered real enough now however since cashed-up and therefore higher-value owners use high-end biometric phones today.
Users of biometrics-equipped phones will do well to upgrading to a supported and recent ROM, which given the telco and vendor patch bottleneck probably means moving older devices to custom operating systems like CynaogenMod. If that sounds a bit weird or scary, know that the community-coded Android variant claims more users than BlackBerry and Windows Phone combined.
The team found a forehead-slapping flaw in HTC One Max in which fingerprints are stored as an image file (dbgraw.bmp) in a open "world readable" folder.
"Any unprivileged processes or apps can steal user’s fingerprints by reading this file," the team says, adding that the images can be made into clear prints by adding some padding.
It is one of four vulnerability scenarios in which biometric data normally secure in an Android phone's TrustedZone can be pilfered.
One such scenario shows how attackers can have money transfers authenticated by throwing a fake lock screen prompting a victim to scan their fingerprints to unlock a device.
Yulong Zhang, Zhaofeng Chen, Hui Xue, Tao Wei say in the paper Fingerprints On Mobile Devices: Abusing and Leaking [PDF] presented at Black Hat in Las Vegas last week that most device manufacturers fail to use Android's Trust Zone protection to safeguard biometric data.
They say they are likely the first to reveal the threat.
"To make the situation even worse, each time the fingerprint sensor is used for auth operation, the auth framework will refresh that fingerprint bitmap to reflect the latest wiped finger," the team says.
"So the attacker can sit in the background and collect the fingerprint image of every swipe of the victim."

The team say attackers with some remote code execution exploits in hand can harvest these fingerprints en masse.
Attackers could in a probably less likely scenario add their fingerprints to a device which they have physical access to by uploading a print image. A disconnect between the number of authorised prints and actual authorised prints means the uploaded biometric could be seen as a "backdoor", the team says.
The researchers point out that this is a very serious mistake by citing research predicting that fingerprint scanners will exist in about half of all phones sold in 2019.
The risk could be considered real enough now however since cashed-up and therefore higher-value owners use high-end biometric phones today.
Users of biometrics-equipped phones will do well to upgrading to a supported and recent ROM, which given the telco and vendor patch bottleneck probably means moving older devices to custom operating systems like CynaogenMod. If that sounds a bit weird or scary, know that the community-coded Android variant claims more users than BlackBerry and Windows Phone combined.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.