Tuesday, September 30, 2014
ISMS Defined in terms of security
ISMS can be defined as the processes used by management to organize and coordinate security activities like governance, risk management, continuous improvement, internal audit, record keeping, document management, compliance management, communications, and awareness training. ISMS is defined in detail within mandatory clauses 4 - 10.
ISMS mitigates a series of common risks to information management but applying an internationally set of control objectives listed in Annex A. Annex A is an appendix of ISO 27001. Annex A control objectives are discretionary and can be risk justified in or out of scope.
There are over 140 contributing countries and thousands of information security professionals over a period of two years that rationalized and contributed to the latest version ISO 27001:2013. Since its inception in 1995 as BS7799 and then ISO 17799 there have been thousands more to establish ISO 27001 as the only internationally accepted information security management framework standard.
Monday, September 29, 2014
Is that true NSA Patents are available to buy
There's a new article on NSA's Technology Transfer Program, a 1990s-era program to license NSA patents to private industry. I was pretty dismissive about the offerings in the article, but I didn't find anything interesting in the catalog. Does anyone see something I missed?My guess is that the good stuff remains classified, and isn't "transferred" to anyone.
Quest to Open-Source Cancer Research
Sunday, September 28, 2014
Security Concern with icloud
This is a good essay on the security trade-offs with cloud backup:iCloud backups have not eliminated this problem, but they have made it far less common. This is, like almost everything in tech, a trade-off:It's true. For most people, the risk of data loss is greater than the risk of data theft.
Ideally, the companies that provide such services minimize the risk of your account being hijacked while maximizing the simplicity and ease of setting it up and using it. But clearly these two goals are in conflict. There's no way around the fact that the proper balance is somewhere in between maximal security and minimal complexity.
- Your data is far safer from irretrievable loss if it is synced/backed up, regularly, to a cloud-based service.
- Your data is more at risk of being stolen if it is synced/backed up, regularly, to a cloud-based service.
Further, I would wager heavily that there are thousands and thousands more people who have been traumatized by irretrievable data loss (who would have been saved if they'd had cloud-based backups) than those who have been victimized by having their cloud-based accounts hijacked (who would have been saved if they had only stored their data locally on their devices).
It is thus, in my opinion, terribly irresponsible to advise people to blindly not trust Apple (or Google, or Dropbox, or Microsoft, etc.) with "any of your data" without emphasizing, clearly and adamantly, that by only storing their data on-device, they greatly increase the risk of losing everything.
Shellshock Vulnerability Gone Wild
It's a big and nasty one.Invariably we're going to see articles pointing at this and at Heartbleed and claim a trend in vulnerabilities in open-source software. If anyone has any actual data other than these two instances and the natural human tendency to generalize, I'd like to see it.
Patient Record Worth More Than Credit Card Value
There's a Reuters article on new types of fraud using stolen medical records. I don't know how much of this is real and how much is hype, but I'm certain that criminals are looking for new ways to monetize stolen data.Saturday, September 20, 2014
Screen Capture using VLC
How to record your desktop activity using VLC in Ubuntu – Steps
a) Launch VLC (Gnome: Application -> Sound and Video -> VLC Media Player | Unity Dash: Search for VLC)b) Click on the ‘Screen Capture’ on the left side items. After you do that, in the playlist section, ‘Desktop’ item would be listed.

c) Right click on the ‘Desktop’ item and click ‘Save’, a ‘Convert’ window should open. At this point we are not yet started the recording and telling VLC the file name where the screen capture video would be stored.

d) In the ‘Convert’ window, do the followings:
-> Choose your desired recording file format from ‘Profile’ drop down.
-> In the destination section, click Browse and choose a file name.

VLC Support below file formats catering to almost all popular types:

e) Now, click Start button in the ‘Convert’ window and the screen recording processing would start. Whatever you are doing on the desktop would be recorded and being saved in the file name you chose.
f) To stop the recording, Click the STOP button in the main VLC Player window.
g) Once it is stopped, go to the directory where you have kept your recording file and play using any media player.
Secretly monitoring your conversations
Earlier this month, there were a bunch of stories about fake cell phone towers discovered around the US These seems to be IMSI catchers, like Harris Corporation's Stingray, and are used to capture location information and potentially phone calls, text messages, and smart-phone Internet traffic. A couple of days ago, the Washington Post ran a story about fake cell phone towers in politically interesting places around Washington DC. In both cases, researchers used by security software that's part of CryptoPhone from the German company GSMK. And in both cases, we don't know who is running these fake cell phone towers. Is it the US government? A foreign government? Multiple foreign governments? Criminals?This is the problem with building an infrastructure of surveillance: you can't regulate who gets to use it. The FBI has been protecting Stingray like its an enormous secret, but it's not a secret anymore. We are all vulnerable to everyone because the NSA wanted us to be vulnerable to them.
We have one infrastructure. We can't choose a world where the US gets to spy and the Chinese don't. We get to choose a world where everyone can spy, or a world where no one can spy. We can be secure from everyone, or vulnerable to anyone. And I'm tired of choosing surveillance over security.
Article on polyalphabetic stream cipher
If there's anything that confuses wannabe cryptographers, it's one-time pads.Protest Against PRISM Yahoo's Role
In 2008, Yahoo fought the NSA to avoid becoming part of the PRISM program. It eventually lost the court battle, and at one point was threatened with a $250,000 a day fine if it continued to resist. I am continually amazed at the extent of the government coercion.Even Captcha can be a evidence to identify the culprit
According to court documents, Dread Pirate Roberts was identified because a CAPTCHA service used on the Silk Road login page leaked the users' true location.When the FBI took down the online black market and drug bazaar known as the Silk Road, privacy activists and security experts have traded conspiracy theories about how the U.S. government managed to discover the geographic location of the Silk Road Web servers. Those systems were supposed to be obscured behind the anonymity service Tor, but as court documents released Friday explain, that wasn’t entirely true: Turns out, the login page for the Silk Road employed an anti-abuse CAPTCHA service that pulled content from the open Internet, thus leaking the site’s true location.
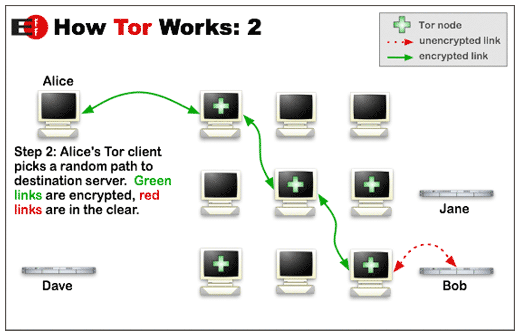
Tor helps users disguise their identity by bouncing their traffic between different Tor servers, and by encrypting that traffic at every hop along the way. The Silk Road, like many sites that host illicit activity, relied on a feature of Tor known as “hidden services.” This feature allows anyone to offer a Web server without revealing the true Internet address to the site’s users.
That is, if you do it correctly, which involves making sure you aren’t mixing content from the regular open Internet into the fabric of a site protected by Tor. But according to federal investigators, Ross W. Ulbricht — a.k.a. the “Dread Pirate Roberts,”
the 30-year-old arrested last year and charged with running the Silk Road — made this exact mistake.
As explained in the Tor how-to, in order for the Internet address of a computer to be fully hidden on Tor, the applications running on the computer must be properly configured for that purpose. Otherwise, the computer’s true Internet address may “leak” through the traffic sent from the computer.
And this is how the feds say they located the Silk Road servers:
“The IP address leak we discovered came from the Silk Road user login interface. Upon examining the individual packets of data being sent back from the website, we noticed that the headers of some of the packets reflected a certain IP address not associated with any known Tor node as the source of the packets. This IP address (the “Subject IP Address”) was the only non-Tor source IP address reflected in the traffic we examined.”For many Tor fans and advocates, The Dread Pirate Roberts’ goof will no doubt be labeled a noob mistake — and perhaps it was. But as I’ve said time and again, staying anonymous online is hard work, even for those of us who are relatively experienced at it. It’s so difficult, in fact, that even hardened cybercrooks eventually slip up in important and often fateful ways (that is, if someone or something was around at the time to keep a record of it).
“The Subject IP Address caught our attention because, if a hidden service is properly configured to work on Tor, the source IP address of traffic sent from the hidden service should appear as the IP address of a Tor node, as opposed to the true IP address of the hidden service, which Tor is designed to conceal. When I typed the Subject IP Address into an ordinary (non-Tor) web browser, a part of the Silk Road login screen (the CAPTCHA prompt) appeared. Based on my training and experience, this indicated that the Subject IP Address was the IP address of the SR Server, and that it was ‘leaking’ from the SR Server because the computer code underlying the login interface was not properly configured at the time to work on Tor.”
A copy of the government’s declaration on how it located the Silk Road servers is here (PDF). A hat tip to Nicholas Weaver for the heads up about this filing.
Signalling System No. 7 vulnerability
What's interesting about this story is not that the cell phone system can track your location worldwide. That makes sense; the system has to know where you are. What's interesting about this story is that anyone can do it. Cyber-weapons arms manufacturers are selling the capability to governments worldwide, and hackers have demonstrated the capability.Know more about SS7 protocol
Apple Claims As Security
Apple claims that they can no longer unlock iPhones, even if the police show up with a warrant. Of course they still have access to everything in iCloud, but it's a start.Wednesday, September 17, 2014
Faster Development With Ruby On Rails
-
CoC:
-
DRY (Do not Repeat Yourself):
-
Object-Oriented Nature :
-
Gems:
-
Built In Tools :
-
Readable Code :
-
Automated Testing :
-
Caching :
-
Localization:
-
Time Cutting:
-
Use RAKE and SAVE Time :
-
Active Record:
Tuesday, September 16, 2014
NSA workaround google earth
According to top-secret documents from the NSA and the British agency GCHQ, the intelligence agencies are seeking to map the entire Internet.Furthermore, every single end device that is connected to the Internet somewhere in the world — every smartphone, tablet and computer — is to be made visible. Such a map doesn't just reveal one treasure. There are millions of them. The breathtaking mission is described in a Treasure Map presentation from the documents of the former intelligence service employee Edward Snowden which SPIEGEL has seen. It instructs analysts to "map the entire Internet — Any device, anywhere, all the time." Treasure Map allows for the creation of an "interactive map of the global Internet" in "near real-time," the document notes. Employees of the so-called "FiveEyes" intelligence agencies from Great Britain, Canada, Australia and New Zealand, which cooperate closely with the American agency NSA, can install and use the program on their own computers. One can imagine it as a kind of Google Earth for global data traffic, a bird's eye view of the planet's digital arteries.
Still 90 days more for meta data collection
schwit1 sends word that the Foreign Intelligence Surveillance Court has authorized a 90-day extension to the NSA's ability to collect bulk metadata about U.S. citizens' phone calls. In April, the House of Representatives passed a bill to limit the NSA's collection of metadata, but the Senate has been working on their version of the bill since then without yet voting on it. Because of this, and the alleged importance of continuing intelligence operations, the government sought a 90-day re authorization of the current program. The court agreed. Senator Patrick Leahy said this clearly demonstrates the need to get this legislation passed. "We cannot wait any longer, and we cannot defer action on this important issue until the next Congress. This announcement underscores, once again, that it is time for Congress to enact meaningful reforms to protect individual privacySecurity Stories In Lines Of New Zealand
New Zealand is spying on its citizens. Edward Snowden weighs in personally.
The NSA and GCHQ are mapping the entire Internet, including hacking into Deutsche Telekom.
Monday, September 15, 2014
Probing Security Kill Hash Function
Good article on the insecurity of SHA-1 and the need to replace it sooner rather than later.
Concern About Data Collection
Since the beginning, data privacy regulation has focused on collection, storage, and use. You can see it in the OECD Privacy Framework from 1980 (see also this proposed update).Recently, there has been concerted effort to focus all potential regulation on data use, completely ignoring data collection. Microsoft's Craig Mundie argues this. So does the PCAST report. And the World Economic Forum. This is lobbying effort by US business. My guess is that the companies are much more worried about collection restrictions than use restrictions. They believe that they can slowly change use restrictions once they have the data, but that it's harder to change collection restrictions and get the data in the first place.
We need to regulate collection as well as use. In a new essay, Chris Hoofnagle explains why.
Will Apple Pay Be An Alternate To CCards
Sunday, September 14, 2014
Evolution Of New GRC
While GRC is ultimately about collaboration and communication between the business roles and processes responsible for varying risk and compliance functions, there is no doubt that technology has an important role in facilitating this enterprise cooperation.I have put together a new high-level framework addressing GRC and its components.
- Enterprise GRC Architecture/Applications. Represent the solution areas that span risk and compliance roles and processes that organizations can leverage and use as the backbone for a GRC strategy. The technology categories in this area are listed below in brief definition. These solutions are not locked to a single role but something multiple roles/business functions/processes can leverage. I feel this area is fairly solid
- Role specific Applications. This provides a list of GRC related roles within the organization and specific application categories that serve these specific roles. There is still much to be built out in this area and would appreciate your feedback on these specific roles and the application categories that serve them. There are some technologies, such as audit management, that are essential for a strong GRC strategy - but they serve primarily a single role, audit.
- Industry Specific Applications. It is in this category that applications/technologies aimed at a specific industry vertical are mapped. An example is the several technology providers aimed specifically at helping life sciences companies comply with GxP. Or there are other solutions aimed at Medicare/Medicaid RAC audits. Or NERC in the utility space. This area has a lot that can be built out. I would love your feedback on getting to a standard for representing industries that is not too narrow nor broad. I would also appreciate your feedback and experience on applications focusing on specific industry issues.
- Geography/Legal Jurisdiction Applications. This is the most rough, and I am not sure how it will be built out. This is the thought that there are specific legal jurisdictions that might require a specific solution for GRC purposes. Thoughts?
- Technology Architecture Components. This is a listing of feature/functionality that any given product in any of these areas might bring together to deliver a solution. It also may represent the IT platform/architecture tools that organizations can build their own GRC platforms out of if they were not going to invest in a commercial product. As for commercial products, a buyer should be able to evaluate them and identify if such technology components as content management, workflow, and other components are part of the platform being implemented/considered. Of course, varying GRC related solutions (and there are over 500 vendors and 1000+ products in this space) can be utlizied in a variety of technology delivery capabilities such as software as a service, hosted application, or traditional software model.
- Accountability Management. This provides an enterprise platform to manage the accountability/ownership of risks, controls, policies, incidents/loss, and GRC related processes. Every silo of risk and/or compliance should have someone accountable as well as specific policies, investigations, loss, risks, assessments, etc.
- Assessment & Survey Management. This is the enterprise platform for delivering a common assessment and survey tool/process. Of course, at a basic level this could be spreadsheets - and often are. At the right implementation level it is a consistent tool to deliver, track, and record survey/assessments for risk, control, and compliance purposes.
- Asset/Process/Entity Register/Taxonomy. If you think about it - every risk, control, policy, loss, requirement applies to something in the organization. It is important that organizations have an ability to model their organization structure, roles/employees, business relationships, processes, physical environment, logical environment, and information. From there - risks, controls, policies, and so forth can be applied to the assets/processes they apply/belong to.
- Continuous Control Monitoring/Automation/Enforcement. This is the category to provide an enterprise platform for the continuous monitoring and automation of controls - both preventive and detective. This includes continous/automated monitoring of (1) IT infrastructure, (2) application permissions, (3) records/data, and (4) business transactions.
- Control Registry/Taxonomy. It is here that the organization provides a catalog of its controls, as well as versioning of controls to provide a history/audit trail. It is in this category that the broad spectrum of controls is defined and managed.
- GRC Dashboard & Reporting. This is the core capability necessary to analyze and report on the breadth of GRC related data across the enterprise.
- Hotline/Helpline. It is here the organization deploys a centralized web-reporting and/or call center where employees, clients, partners, stakeholders can report wrong doing and/or suspicious activity as well as seek help on certain compliance, risk, ethics, and code of conduct topics.
- Identity & Access Management. My research this past year has caused me to elevate this to an enterprise issue, and not just an IT risk and compliance category. Organizations need an enterprise approach to cataloging identities, access, entitlements to both the physical and logical business environments. If you think about it, a lot of risk and compliance issues comes down to who has access to what, what can they do with it, etc.
- Investigations/Incident/Loss Management. This represents an enterprise platform/ability to consistently document and manage the process/workflow of investigations. It also provides a common platform for tracking and monitoring losses the organizations has experienced.
- Policy & Procedure Management. It is here an organization builds/delivers a solution to provide a consistent interface and user experience to manage the development, approval, communication, maintenance, and archiving of corporate policies and procedure documents. This also includes training management related to those policies and procedures.
- Requirements Register/Taxonomy. It is in this category that organizations document and breakout the specific chapter and verse of regulatory, legal, and standard guidance. This is the registry that defines the mandatory and voluntary boundaries by which the company is governed - it defines the lines that should not be crossed and what is required of individuals, processes, business relationships, etc.
- Risk & Regulatory Intelligence. Organizations need the ability to monitor the internal context of risk and compliance as well as the external context that business operates within. This represents the category of technologies that can take information from data feeds and turn them into tasks/workflows routed to the right individual to make a decision on a changing business, risk, and/or regulatory environment and how it impacts the organization.
- Risk Analytics & Modeling. Some might see this as part of GRC dashboards and reporting, but the area is complex and can stand on its own. This represents the organizations ability to display and model risk. At a simple level it is heatmaps, at a complex level it may involve monte carlo simulations, bayesian modeling, or value at risk.
- Risk Register/Taxonomy. This represents the enterprise catalog of risks. Like the other register/taxonomy items above the purpose is to not only define, but also to cross-reference risks to loss, policies, controls, assessments, etc.
Friday, September 12, 2014
Integrating Information Security with Project Management
If someone were to try and convince me that the project manager of a non-security specific strategic initiative would hold security priority above business objectives I would have to say that will never happen! After all business requirements drive information security needs and information security professionals are business enablers.
This is why the adoption of the ISO 27001 management system with a governance committee overseeing the security program is fundamental if that governance committee represents the Executive portfolios across the organization and not just IT. The integration of control points defined in Annex A is equally crucial to ensuring that information security is seamless..
One of my more successful strategies is to collaboratively develop a one page risk assessment for the project manager to facilitate. Its added to a list of required PMO documents for every project. The 10 - 12 questions are weighted and if the conclusion exceeds a threshold the Information Security Office is engaged, if it doesn't the project carries on. Any risks that are identified are added to the project risk registry. The information security office audits the projects regularly to see if the process is working and if its being followed. Awareness training is provided to the project managers.
Why To Adopt A VPN
Here are three words for you: Virtual Private Network (more commonly referred to as VPN). If you’ve never heard of the term, or aren’t sure about its exact nature in our info tech world, then chances are you’ve never utilized one. A VPN is facilitated for several reasons, by individuals and the business sector alike. Anyone who initiates one for their time on the internet will have a variety of reasons. They can vary according to the individual’s needs and wants; scaling from minimal personal usage to access international television programs not available in their region, to encryption and security during time spent in cyberspace. In essence, a VPN is used to secure and encrypt communications when using an untrusted network which is in the public domain.The latter is the more common theme. In this day and age where big brother seems to lurk in every corner of our internet browser, more and more people, and companies, are resorting to the use of a VPN provider. In fact, as people are educating themselves on the realms of the digital jungle that is fast becoming a second home, the VPN is becoming a common household name.
And why not? With hackers at the ready to steal your sensitive information, and government regimes watching and monitoring your every move, the VPN is now an essential addition to add to our daily internet rituals. In essence, public networks are cesspits, and if we dwell in them too long, without the correct protective elements, then we tend to ‘pick up’ those bugs which dwell in them.
When you use a VPN, the usual presentation is to launch a VPN client on your personal computer. You log in; your computer then “exchanges trusted keys with a server,” and once both systems have been authentically verified, your communication on the internet is secure.
However, not all VPNs are created equally. When searching for the right VPN for your own use, it is important to know what it is you are signing up for, and who with. You need to take into consideration connectivity protocols, features and server locations. The best VPNs will offer a good selection on these criteria. Most importantly, the VPN Provider should have a so called ‘no-logging policy’ which ensures that no user activity will be logged.
You need to be aware of other considerations such as trusting your provider with your data. In other words, what do they log? Everything outside of your VPN server is secure from eavesdropping, but those sharing the same provider may have access to your data. Some VPN providers keep logs in case a government requests them, so decide what is acceptable to you when it comes to logging.
I recommend IPVanish as it fulfills all criteria regarding speed, security, support of all mobile devices and most importantly anonymity and safety: “IPVanish does not collect or log any traffic or use of its Virtual Private Network service”
Other features you may want to consider are:
- Does your VPN provider offers Anti Malware/Spyware?
- Do you have the option of securing your phone along with your computer via Mobile Apps?
- Pricing of the provider.
- Exit Servers if you want a country specific VPN.